Security Protection
State-of-the-art Malware Analysis, External Threat Hunting, and Brand Vulnerability Assessment
Level up your cybersecurity with robust protection solutions and
hassle-free support from Domitek
Like most modern-day entrepreneurs, you have likely invested in top-of-the-line firewalls, anti virus, and data backup solutions. But with cybercriminals working around the clock, you also need proactive measures like threat analysis and threat hunting to uncover any loopholes in your cybersecurity so you can address them in time. And that’s what our Security Protection services are designed to do.
We deliver
24/7 Availability
Ongoing operations at all times, both proactively and on-demand per the customer’s specific needs.
Alert Monitoring
Continuous management of incoming alerts: classify, prioritize and contact the customer upon validation of active threat.
Exclusions, Whitelisting
and Tunneling
Adjusting Cynet 360 alerting mechanisms to the customers’ IT environment to reduce false positives and increase accuracy.
Threat Hunting
Proactive search for hidden threats leveraging Cynet 360 investigation tools and over 30 threat intelligence feeds.
On Demand Analysis
Customers can send suspicious files to analysis directly from the Cynet 360 console and get an immediate verdict.
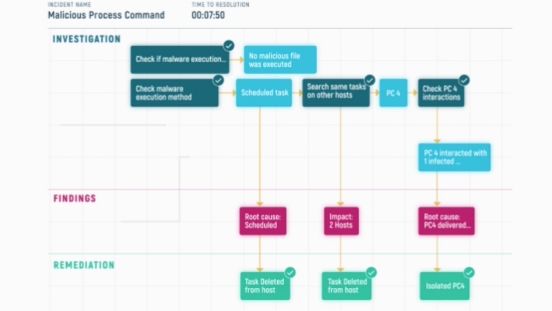
Attack Investigation
Deep-dive into validated attack bits and bytes to gain the full understanding of scope and impact, providing the customer with updated IoCs.
Remediation Instructions
Conclusion of investigated attacks entails concrete guidance to the customers on which endpoints, files, user and network traffic should be remediated.
We Are One Click Away
CISOs can engage CyOps with a single click on the Cynet Dashboard App upon suspicion of an active breach.
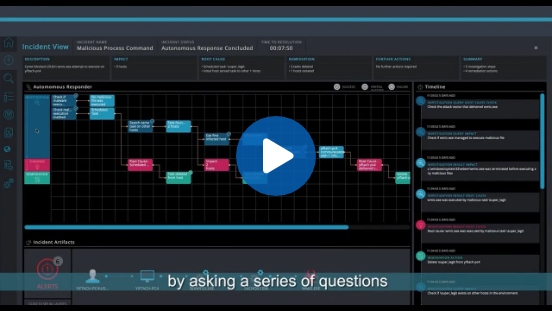
With cyberattacks becoming increasingly sophisticated, having cutting-edge threat detection software is no longer enough to keep your business safe. You need current, actionable threat intelligence data and proactive threat hunting to keep up with cybercriminals. Domitek delivers these tools through a complete bundle of Security Protection services.
We use enterprise-grade security intelligence tools from Cynet and our years of experience and expertise to uncover the weaknesses in your cybersecurity posture and address them with targeted solutions.
With Security Protection from Domitek, you get:
- Thorough assessments – we’ll take a deep look at the nature of your operations and the unique risks you are exposed to
- Clear visibility into your cybersecurity performance – our detailed findings help you see the underlying gaps in your defense scheme
- Multi-layered security plan – our consultants will help you develop an all-encompassing defense scheme that will keep advanced threats at bay
Leverage next-gen detection and prevention capabilities across your networks and endpoints on a single XDR software
XDR (Extended Detection and Response) is a unified cybersecurity platform that combines threat detection and automated incident response capabilities. It provides powerful visibility as well as deception technology across all networks, user activities, and endpoints, and launches automated investigation and appropriate remediation after each attack alert.
Swift detection
Thanks to round-the-clock network traffic monitoring and intuitive threat alert that maximizes accuracy
In-depth investigation
Automated search that helps you grasp the root cause and full impact of each attack quickly
Automated, custom response
Pre-built and custom remediation tools for each particular endpoint to minimize manual work, delays, and damage
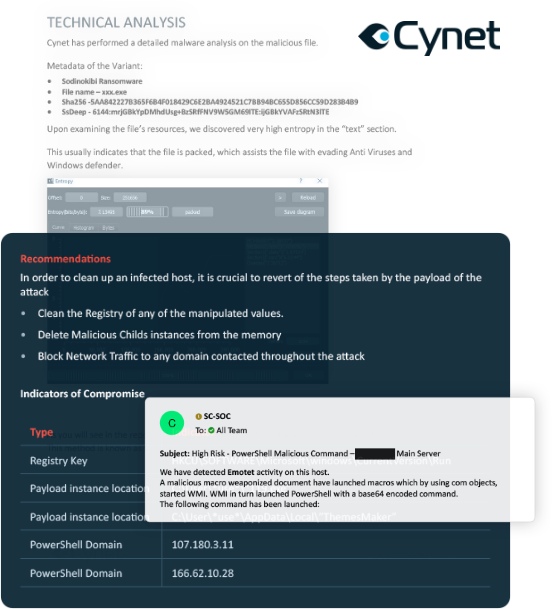
Malware Analysis
In-depth investigation to uncover hidden breaches or malware in your network
Think you can completely count on a threat scanner to detect any malware before it penetrates your network? Think again. Sophisticated malware have managed to slip past layers of security and caused subtle, yet irreversible damages to countless companies over time.
Find any unidentified threat and act before it’s too late with our Malware Analysis.
Identification of Indicators of Compromise (IOCs) and unique threats such as industry adversaries
Determination of damage level and remediation steps
Expert advice on how to put reliable Incident Response plans in place
External Threat Hunting
A proactive search to detect, contain, and eliminate cyberattacks
Relying exclusively on firewalls and anti-virus software is no longer enough to keep advanced threats at bay. You also need a hacker’s insight on your cybersecurity vulnerabilities, and a detailed visibility into how effective your response solutions are so you can ensure prompt threat containment and minimal disruption to your systems.
Insight into your cybersecurity environment through an attacker’s point of view
Prompt identification and containment of new threats to minimize security breach risks
Clear visibility on potential threats thanks to metadata that is mapped with threat signals
Validation on the effectiveness of threat response solutions to ensure no additional damage on your systems
Brand Vulnerability Assessment (BVA)
Extensive analysis of cyber risks to your company’s online presence
A BVA is a series of tests that help you understand the security threats that come with your business’s digital exposure such as phishing domain risk, and adds valuable insight to your potential M&A research.
Clear understanding of your organization’s digital exposures and its vulnerabilities
Round-the-clock threat monitoring
Detailed reports that can be leveraged for M&A research to pinpoint specific risks from business acquisition